Prism Deploy and Prism Pack ship with Group Policy template files that when enabled will prevent the unauthorized installation of Prism Packages (.pwc), Self-Installing Files (.exe) and the unauthorized running of Prism scripts (.pts) and subscription files (.pwsubs and .exe).
Steps to Secure Prism Installations
The following items are well known network security ”best practices”:
- Do not give users local or domain administrative rights. Only those responsible for managing the network and who understand the implications of their actions should be given local or domain administrator rights.
- Do not give users access to the registry.
- Keep all systems (servers and workstations) patched with the latest security patches, service packs, hotfixes, etc.
- Enforce the use of secure passwords on all workstations and servers, and require that passwords are changed on a regular basis.
The next steps enable you to further lock down the use of Prism Deploy:
- Password-protect all Prism Deploy Channels. Keep the passwords secure and change them on a regular schedule.
- Use Prism-specific Group Policy templates on Active Directory-enabled servers to prevent the Prism client from executing via the command line and to lock down other aspects of the client installation. The Prism templates are in a subfolder named GroupPolicy in the installation folder for the Prism product. Either share this folder or copy it to a location that is accessible from your domain controller server.
· At your Windows 2000 or Windows 2003 Servers, open “Active Directory Users and Computers”.
· Select the root of your domain (e.g., SERVER.domain.local). Open Properties.
· Select the Group Policy tab.
· Create a new Group Policy Object and give it a descriptive name, such as “PrismClientLockDown”.
· Select Edit and browse to Computer Configuration | Administrative Templates. Right-click on Administrative Templates and choose Add/Remove Templates, then browse to the Prism.adm or PrismPack.adm file in the GroupPolicy folder. Figure 1 shows the template loaded in MMC.
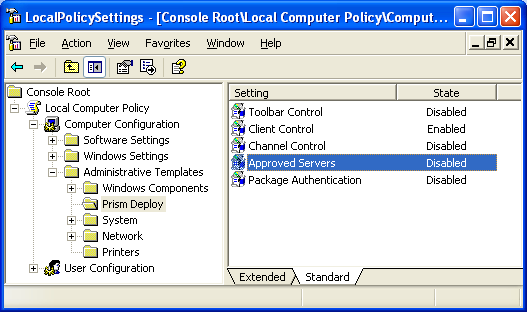
Figure 1
Note: The policy setting for Package Authentication using digital certificates to sign all packages is detailed in the Prism Editor compiled help file. Browse to the help file in the related links section below, then (search for “digital signature”).
· Once the template is added, open the Client Control policy. Enable it, and make the choices shown below. The setting “Disable Ability to Use Client Command Line” prevents the unauthorized installation of Prism Packages (.pwc), Self-Installing Files (.exe) and the unauthorized running of Prism scripts (.pts) and subscription files (.pwsubs and .exe) – in effect disabling any use of the client except through tasks assigned through the Prism Deploy Console.
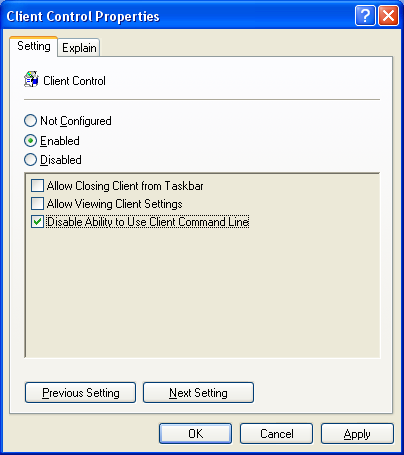
Figure 2
Likewise, enable policies for Toolbar Control, Channel Control, and Approved Servers. The settings shown below are for maximum security.
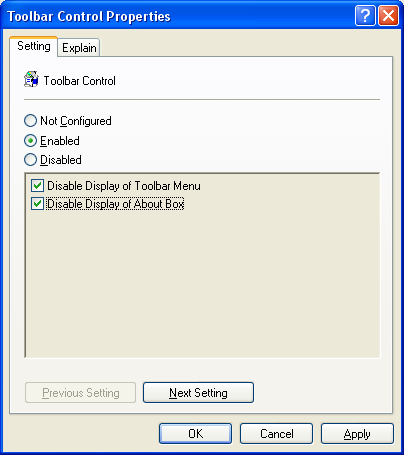
Figure 3
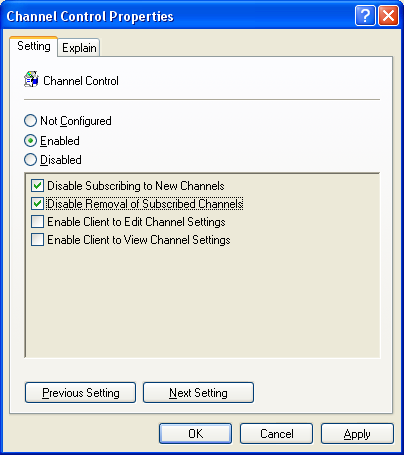
Figure 4
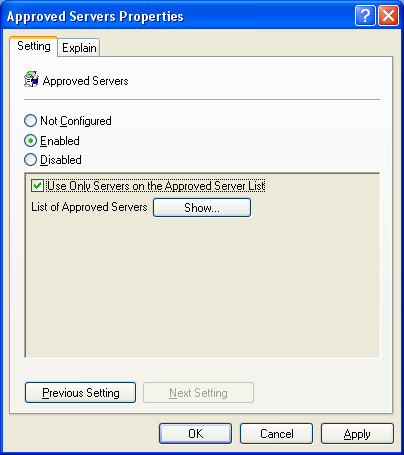
Figure 5
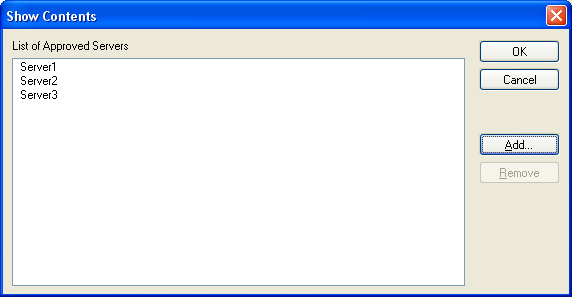
Figure 6
· Save and close all windows.
Prism lock-down settings can be configured by use of a Prism package that modifies the registry. Contact support@newboundary.com if you would like further information.